Cordova Security Considerations
More and more (mobile) apps are written in Apache Cordova (or its proprietary variants such as PhoneGap or SAP Kapsel). Apache Cordova is a framework that allows to easily write (mobile) apps for many different platforms using a hybrid development approach, i.e., combining web development technologies (HTML5 and JavaScript) with native development techniques such as Java or Objective C.
Combining web and native technologies creates new security challenges as, e. g., an XSS attacker becomes more powerful. For example, a XSS vulnerability might allow an attacker to access the calendar of a device or delete the address book.
Overview
On the one hand, Cordova apps are HTML5 applications, i.e., they share all typical features (e.g., JavaScript code that is downloaded at runtime) and security risks (e.g., XSS) of web applications. On the other hand, Cordova apps share the features (e.g., full device access) and security risk (e.g., SQL injections, privacy leaks) of native apps.
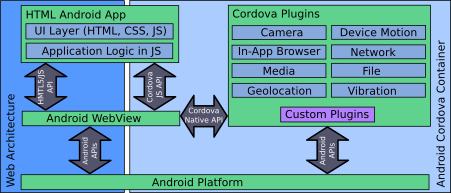
To limit the typical web application threats, WebViews (which execute the HMTML5/JavaScript part of a Cordova app) are re-using the well-known security mechanism from web browsers such as the same-origin policy. Moreover, WebViews are separated from the regular web browsers on Android, e.g., WebViews have their own cache and cookie store. Still, there are subtle differences that make implementing secure Cordova apps even for experienced web application developers a challenge.
A plugin is a mechanism for drilling holes into the sandbox of a WebView, making the traditional web attacker much more powerful as, e.g., an XSS attack might grant access to arbitrary device features. The root cause for such vulnerabilities can be located in Cordova itself (e.g., CVE-2013-4710 or CVE-2014-1882 or in programming and configuration mistakes by the app developer.
Recommendations
Do not forget that Cordova apps are web applications, thus, you need to
- do secure JavaScript programming
- use the content security policy and same origin policy
- always use https and validate SSL certificates, dynamically loaded code from third parties can be dangerous (even if ``iframed’’)
- …
And keep in mind, that the WebView sandbox is not as protective as it is in modern desktop browsers.
Cordova apps are native (Java, Objective C, Swift, .net, …) apps and, thus, you need to apply the best practices of native development, such as:
- do secure Java/Objective-C/… programming
- do not trust validations done in the JavaScript part of the plugin (do input validation in the native part)
- …
Cordova apps are mobile apps, and you need to use the security features of the mobile platform correctly, e.g.,
- do use as few permissions as possible
- …
Finally, Cordova apps are Cordova apps:
- use plugin white-listing (and only ship plugins that you really need)
- if you need only very limited features of a plugin (e.g., read only access to a calendar) it is more secure to remove the unnecessary features in the native part
- read the Cordova security guide
- use the latest version of Cordova
- monitor regularly the NVD for new vulnerabilities
- due to CVE-2013-4710 do not use Cordova on Android below version 4.1
Finally, did you know that
<application android:debuggable="true" />on Android disables the certificate checks in WebViews.


