End-to-End Secure Service Compositions
During the development of software systems, security is often understood as a task for specialists. This is unfortunate, as today any system need to fulfill a large variety of security (and privacy) properties of which many rely on input from domain experts that are often no security experts. To allow security interested developers of service-based systems, e.g., using microservices, we developed a too-supported, model-based approach that allows to capture and analyze security properties on the level of composition models. Moreover, our approach supports “pushing security requirements” down to the implementation level, supporting developers in implementing the services securely.
Modeling and Validating Security Properties
Let’s start top down with the modeling of service compositions. In our prototype, we use BPMN as graphical notation for modeling the actual service composition (as well as user interactions, i.e, manual tasks). The example in the following figure shows a simple service composition implementing a travel booking service:
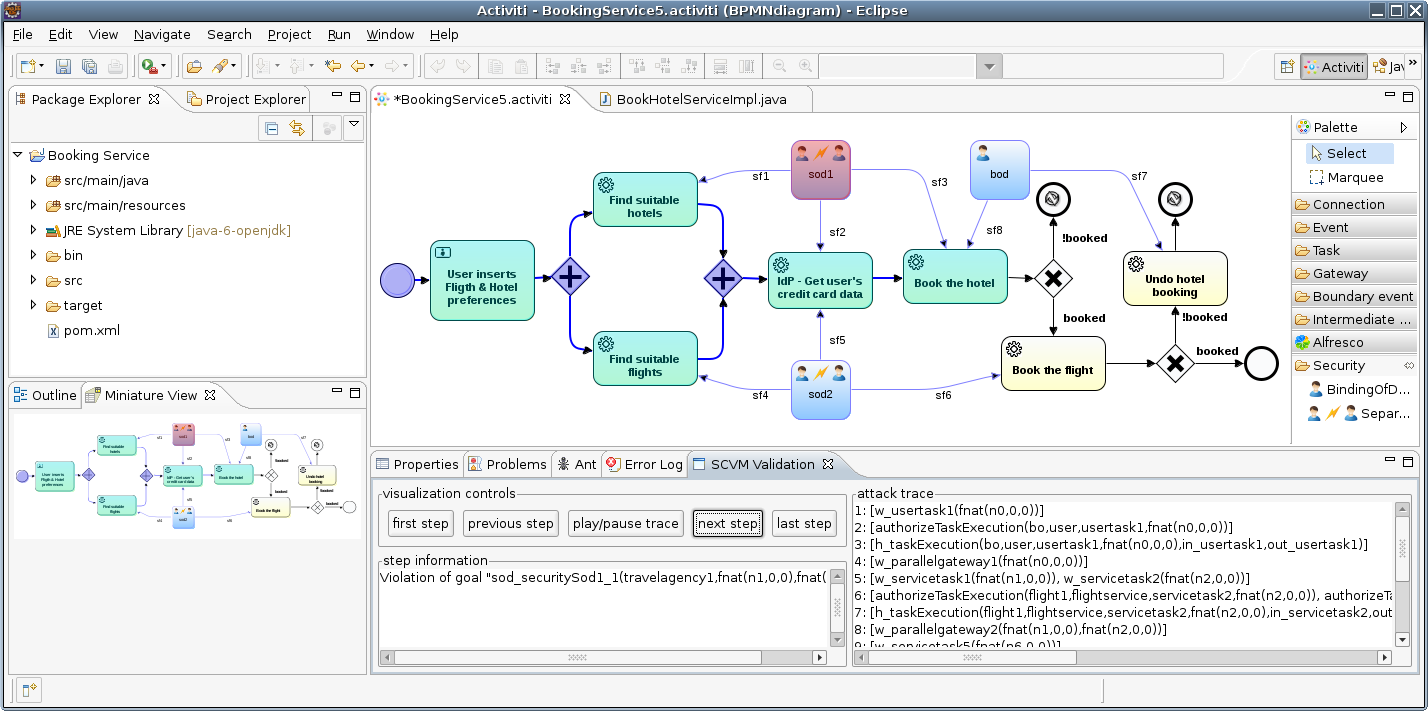
In our approach, the designer of the service composition can, already on this very abstract level, specify several security and privacy properties that need to be fulfilled by the actual system. For example, the service designer can specify who can access (invoke) services using a role-based access control model that also supports separation of duty and binding of duty requirements.
We do not only support the specification of security and privacy properties, our approach allows also to analyze the specified requirements to detect inconsistencies as early as possible in the design phase. Recall our example from the first figure: here, the role-based access control does not enforce the required separation of duty requirement.
Service Quantification and Ranking
Service-based systems are usually implemented by combining already existing services and, if necessary, by implementing services for which no readily-available implementation exists. Our approach supports service designers in selection the most suitable service from service marketplaces by a ranking that includes functional as well as non-functional (i.e., security or performance) requirements.
Implementing Services Securely
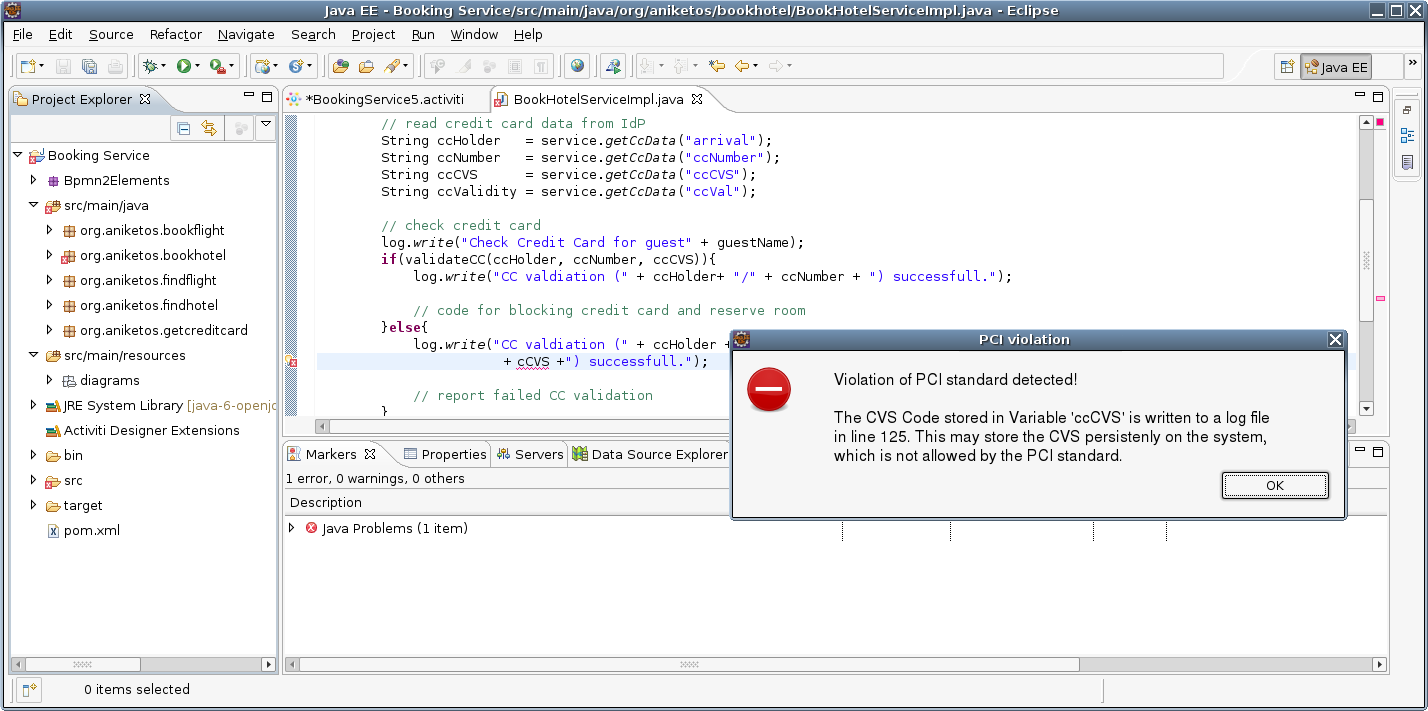
Our approach allows combining model-driven and traditional, code-based, development. This is usually necessary when no readily-available service implementation exists and a bespoke service needs to be developed. In this situation, we derive, from the high-level security specification on the model-level, properties that need to be fulfilled on the code level. These requirements are checked by using static analysis tool that uses project-specific rules that are automatically generated from the high-level models. In the following example, a developer is warned that a service is not correctly handling credit card data:
Conclusion
Clearly, only a relatively small subset of business-related security and privacy requirements can be captures by non-experts. Still, our approach shows that allowing non-experts to specify security properties facilitates the necessary discussion with security experts on how the developed systems can be secured. Moreover, the end-to-end approach ensures that security requirements captures early on in the design-phase are not lost when implementing the system.
Want to learn more? The details are in our paper published in the journal “Software: Practice and Experience (SPE)” [1].


